Domain fronting is a technique that involves using different domain names in the Encrypted Server Name Indication (ESNI) field of the TLS header and the Host field of the HTTP host header. Domain fronting is a useful tool for evading online censorship and accessing the internet freely, but it can also be used by hackers and scammers.
The domain name is translated into an IP by a DNS server and the browser establishes a connection via HTTP or HTTPS. The domain remains the same, and the browser gets connected to the website. Using domain fronting, DNS and TLS will refer to the same domain while the HTTPS level contains a different domain. The HTTPS domain is encrypted, so it can bypass censorship barriers by making it seem as though the DNS and TLS requests contain an unrestricted domain.
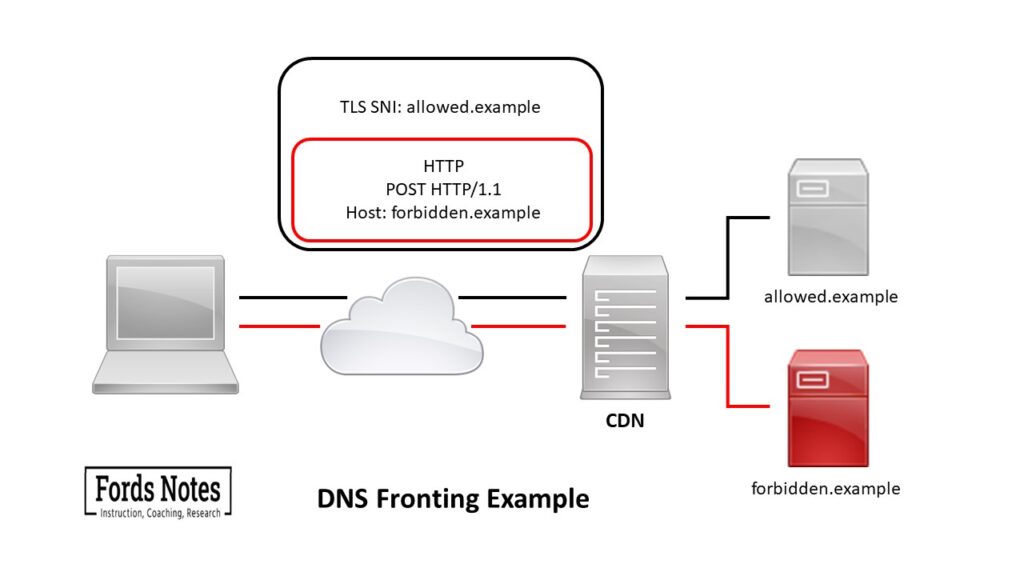
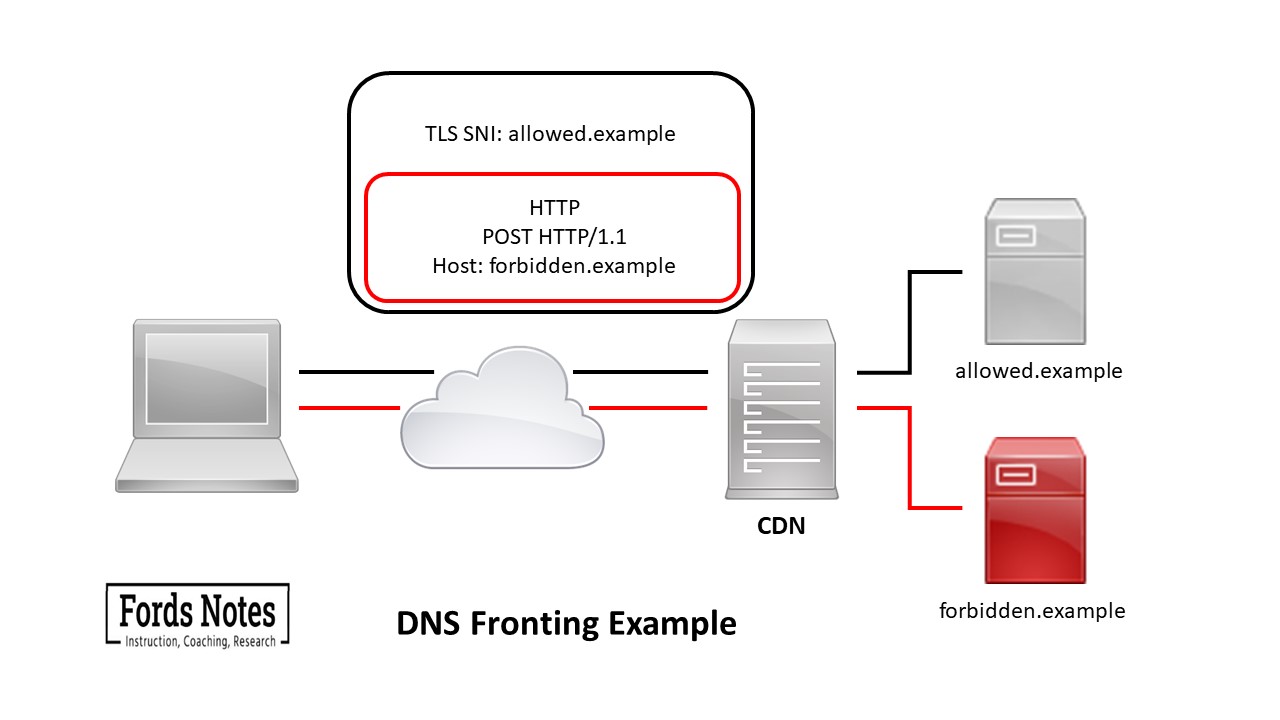
A common domain fronting technique relies on using a CDN (content delivery network). A CDN is a network of proxy servers that distribute online content by creating copies of it on different servers. A single CDN can host many domains and a user can request content from the CDN server closest to them.
A client sends an HTTP request with the actual destination set in the HTTP host header. The DNS query and TLS SNI contain one domain (also known as the front domain) while the HTTPs header, which is hidden from the censor, by HTTPS encryption, contains the forbidden destination.
Private messaging apps like Signal or Telegram and users who live in Internet content restrictive countries use domain fronting to guarantee privacy and to bypass censorship.
References
Domain Fronting 101: What is Domain Fronting and How Does it Work?